Just once in a while, you can’t get into the WordPress dashboard and you need to create a new admin user quickly. You can do it with PHPMyAdmin. Login to PHPMyadmin Goto your WordPress Database table and click on SQL. Then copy and paste the MySQL statements below. Change YOUR USERNAME, PASSWORD, Your Username and […]
Continue reading...
If you want to programmatically insert a post in the front end, for example based on user input, there is a danger that the user can resubmit the form and post it twice. WordPress has the function post_exists to prevent that. But it is an admin function and if you try using it in the […]
Continue reading...
If you need to send a post or page out via email, you will need to parse blocks and shortcodes first. I use MailChimp and the API doesn’t like audio and video tags. This function takes the post content and parses it creating buttons for playing audio and video. In the switch($block[‘blockName’]) you can add […]
Continue reading...
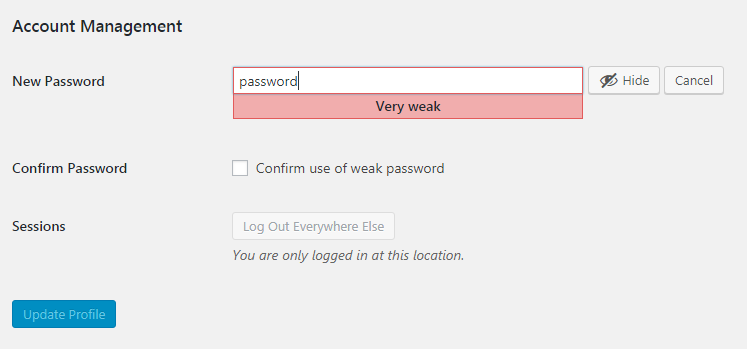
I was once with a client who changed their password for a government website to “password2016” and the website let them do it too! Thankfully, Wordpress gives you a message to warn a user that a password is weak, but it allows users to check a box to override the warning. Noooooo! I don’t want […]
Continue reading...
This evening, I rescued a client’s WordPress website from a hack that was so bad their host shut it down. I have a checklist that I use now to recover WordPress sites, which I’d like to share with you. Or you can hire me to do it for you as it requires some technical confidence! […]
Continue reading...
Sometimes it is a good idea to reset all the passwords for your WordPress website and email the users to let them know their new password. Especially when you have been hacked – if you have been hacked, read about what to do My emergency password reset plugin will regenerate every user’s password and email […]
Continue reading...
If you want your plugin to have a greater reach why not internationalise it – hopefully people will soon start translating it for you! Here’s what to do! Step 1 set up the plugin to load the translation files with this code, changing “your-plugin-name” as needed. //add localisation $my_translator_domain = ‘your-plugin-name’; $my_translator_is_setup = 0; function […]
Continue reading...
If you want to control what image and content Facebook uses when someone likes a post/page on your WordPress site, then add this snippet to your theme functions.php. Any Facebook likes will then use the featured image from that post or page. A similar thing can be done with Twitter – called Twitter cards – […]
Continue reading...