How to rescue a WordPress Hack
 This evening, I rescued a client’s WordPress website from a hack that was so bad their host shut it down. I have a checklist that I use now to recover WordPress sites, which I’d like to share with you. Or you can hire me to do it for you as it requires some technical confidence!
This evening, I rescued a client’s WordPress website from a hack that was so bad their host shut it down. I have a checklist that I use now to recover WordPress sites, which I’d like to share with you. Or you can hire me to do it for you as it requires some technical confidence!
You’d save a lot of heartache, if you backed up your database regularly!
The following step are for when you haven’t and your site is trashed. These should get you back up and running. Take them at your own risk and don’t blame me or sue me – hey your site was trashed anyway!
Gather your account passwords
You’ll need to be able to access PHPMyAdmin and FTP.
PHPMyAdmin is a script on most webhosts control panel that allows you to work on the MySQL database that drives WordPress.
FTP means File Transfer Protocol – it’s the way that you can make changes to the files on your server using a program like Filezilla.
You’ll need usernames and passwords to get into both.
I’m going to assume you know how to use them – if not hire me!
1) Put WordPress in maintenance mode
If your host hasn’t taken the site offline, you’ll want to prevent anyone from doing anything within a wordpress login by putting the site into maintenance mode.
Create a one line php file with the filename .maintenance (just like .htaccess it’ll be a “hidden” file)
the one line you need is
Upload the file to the root directory of the install – usually the same directory as wp-config.php
That forces WordPress into maintenance mode with the message “Briefly unavailable for scheduled maintenance. Try again in a minute.”
2)Change the database passwords
Delete the database user in your webhost control panel and create a new one with a completely different password.
Download the wp-config.php file and edit it. Most wordpress hacks are through a compromised login, where the hacker then uploads a plugin. Assume they know now your db password.
Adjust the wp-config.php lines
/** MySQL database username */
define('DB_USER', '###');
/** MySQL database password */
define('DB_PASSWORD', '###');
Replacing the hashes with the new username and password combination.
Next scroll down to the Authentication Unique Keys and Salts section.
It will look something like this…
define('AUTH_KEY', ' ,b)e~:pL<3.M*0t/Mr*qHeaX(0=@xta+eWnm6bPUSSCc#j4ArAn{{Vyy- a+{.1');
define('SECURE_AUTH_KEY', 'n)sEOj/yP6)4l6NT)IP@!s]h.}rYA7&T7vx!>d%3DZD#<1NrOujz_{p8Kxrz&y=U');
define('LOGGED_IN_KEY', 'qHKk%)Zx=o{JLSkXX?_<KLv4ba.sxWMg!S]gxA]b:=CUBfGkf<%J0OjtZT|U!3;]');
define('NONCE_KEY', '5b7)0{Mq&h?aM!8]{z%?oB&2RiY1S,wYf[dUuZVWfK!%8Fp,9Dk<&;$ey|sjUlg(');
define('AUTH_SALT', 'un[l4T*r;Ol;A.q}@J|9i;gCw(bE=J}/D$k@Xy%u;/?un8s3m<h]?!~b%hVWE~m.');
define('SECURE_AUTH_SALT', '~eIOAeP3+ZWX 9?9%K=M(`-&MkxZ+sRy4|?`u#>x$krb0Jfw.%OtDd!Im J@/M?{');
define('LOGGED_IN_SALT', 'GCgk<xCfR_!)x5E!M( eRh!b0]RDK+e=QYNNw5`y7jQo0kgmiTu[xzBt1a@<q[D`');
define('NONCE_SALT', ':]-.t8H$cG$tN*o,%ne`[J>`UN/`c7l9!,wQgJ~nCcK:=@}um U~QiC:D_/(=w]h');
Changing these will force logout of anyone logged in.
The WordPress boys and girls have provided a useful tool to regenerate these at https://api.wordpress.org/secret-key/1.1/salt/. Don’t be lazy and copy the above 😉
Go ahead and change these in wp-config.php.
Have a quick scan through the rest of the file to check nothing weird is in there. You can compare it to wp-config-sample.php to be sure!
Your wp-config.php is now ready – but don’t upload yet.
3) Delete the current WordPress Install
I think it’s safest to upload a complete fresh install, rather than update.
So delete the following directories – wp-admin, wp-includes and all the files in the root except .htaccess. Do not delete wp-content!
4) Note what plugins and theme were active
If your site is down and you can’t remember which plugins and theme were active then follow this step
Login to PHPMyAdmin and find your WordPress table and click the wp_options (you may have a different prefix than wp_) and then SQL tab
Use the statement SELECT * FROM `wp_options` WHERE option_name = “active_plugins”
Click on edit to see what the value is
It will look something like this
a:7:{i:0;s:19:"PostLikes/index.php";i:1;s:19:"akismet/akismet.php";i:2;s:26:"church-admin-csv/index.php";i:3;s:22:"church-admin/index.php";i:4;s:34:"emergency-password-reset/index.php";i:5;s:34:"never-loose-contact-form/index.php";i:6;s:31:"signup-before-leaving/index.php";}
Yikes! That is a serialized arrray – but I can see PostLikes, akismet, church-admin-csv, church-admin, emergency-password-reset, never-loose-contact-form and signup-before-leaving are the plugin directories of active plugins.
Simpler is finding which theme was active
The SQL statement
SELECT * FROM `gateway_options` WHERE option_name = “current_theme”
will show which theme was active!
5) Clean up the users
Go to the wp_users table and delete any unknown users – especially with date stamps around when your site was hacked.
If you still have an “admin” user – change the username away from admin right NOW! That is likely how the hackers got in!
6) Check the Database for hacked posts and comments…
In phpmyadmin, click your database name at the top, so that all tables are showing and then click “search” – search for “iframe” in all tables
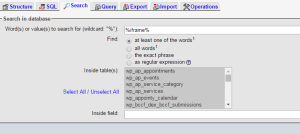
You can then check the entries that show for anything untoward.
7)Clean the wp-content directory
This is where the hacker will have most likely done damage. You should have the directories plugins,themes,upload and upgrade there. Some plugins may have added other directories or even files too.
The index.php file in wp-content should just have
Goto the plugin directory – delete everything! You will upload fresh copies later.
Next the themes directory – again delete everything (careful you have copies of bespoke/child themes stored elsewhere!)
Then go through the uploads directory, by year and month. Delete any .php files – should just be images, pdfs and other user uploaded files.
Delete anything in the wp-content directory that looks suspicious and especially any files ending in .php that don’t look like above.
8) Download fresh copies of plugins and themes
The quickest approach is to download them all as zips, unzip and uplaod back to wp-content/plugins, so that when you get wordpress going again, they are already in their activated state.
9) Download a fresh copy of wordpress from wordpress.org
Unzip all files and upload
9) Upload your prepared wp-config.php files
10) Finally delete the .maintenance file
Delete the .maintenance file from the root directory and you should be live again
I’m happy to help – get in touch for a quote
Does anyone have any other steps they take to clean hacked wordpress sites?