My name is Andy Moyle. I build WordPress websites and plugins. All my websites are “responsive”, which means they are designed to look great on phones, tablets, laptops and desktop
A plugin is a way of adding bespoke features to a website, whether it be a booking system, an SMS reminder service or a contact form. I work with clients to assess what is required, quote cost and timescale and deliver on time.
Glossary for popular WordPress Blog
I look after web development for a political economy blog that has over 29,000 posts and thousands of hits every day. Richard wanted to create a glossary of terms for the site, as an explainer for his readers.
The aim was for automated links for those glossary terms to vbe created when any post was viewed. That turned out to be a pretty complicated task as “accounting policy” in a sentence needed to link to “accounting policy” not the entry for “accounting” or “policy”. The automated linking also needed to ignore images with those words in the url and any links already with those words.
I managed to deliver that in 5 days with 100% accuracy and learned some economics along the way.
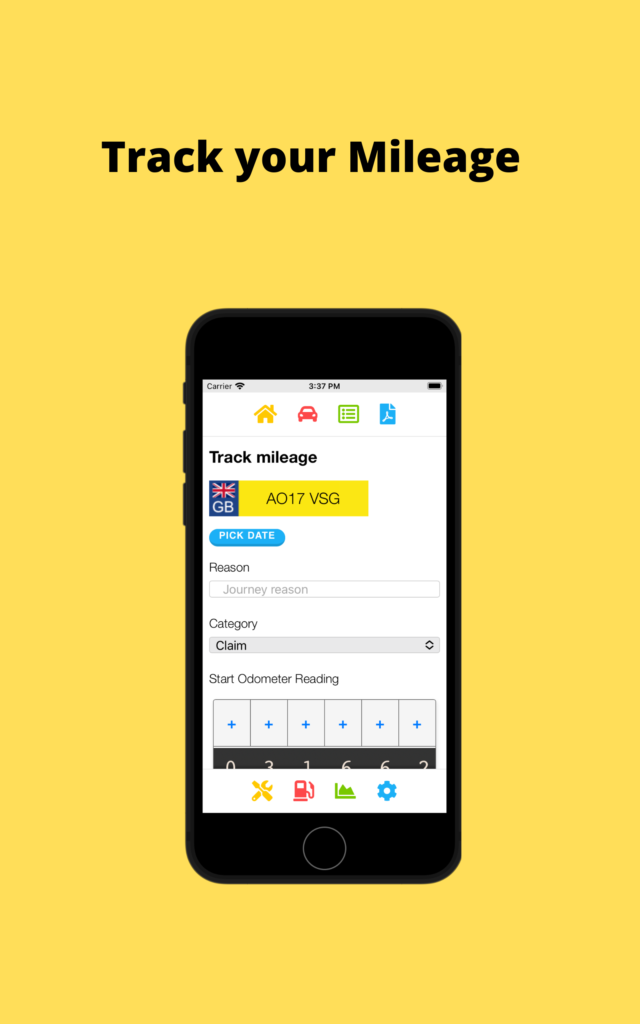
Simple Mileage Tracker App
A lot of the mileage tracker apps are quite expensive subscription based and use mapping, which is drain on data and the battery. So I created a simple app to allow people to track their business mileage journeys in different categories.
You can download and email PDF reports and CSV spreadsheets of the data.
The app also allows fuel efficiency tracking and for UK users checking when MOT and road tax is due.
Head over to www.simplemileagetracker.com for more information and install links. The app is a low one off cost to purchase!
SMS Mot Reminders
A client wanted a plugin so garages could easily remind customers by SMS to book their annual MOT test. He already had 2,000 scheduled messages, so the plugin needed to grab those and allow new ones to be scheduled.
Read the story and see I can help you to with a plugin
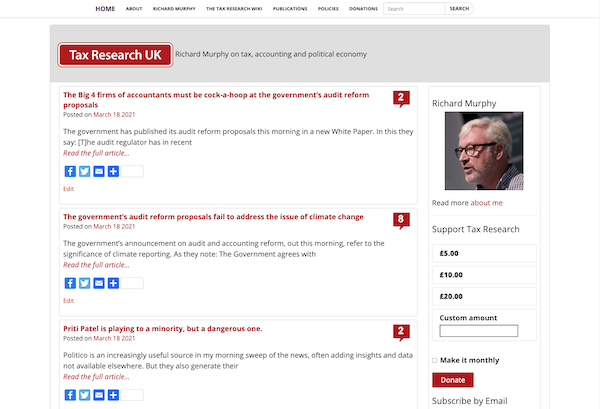
Tax Research blog
Richard Murphy’s blog on Tax is a political blog with high traffic, over 18,500 posts and 200,000 comments. The WordPress theme is simple, fast and responsive – looking great on phones, tablets and desktops.
Given that over 50% of people look at websites on their phone – mobile first design is important!
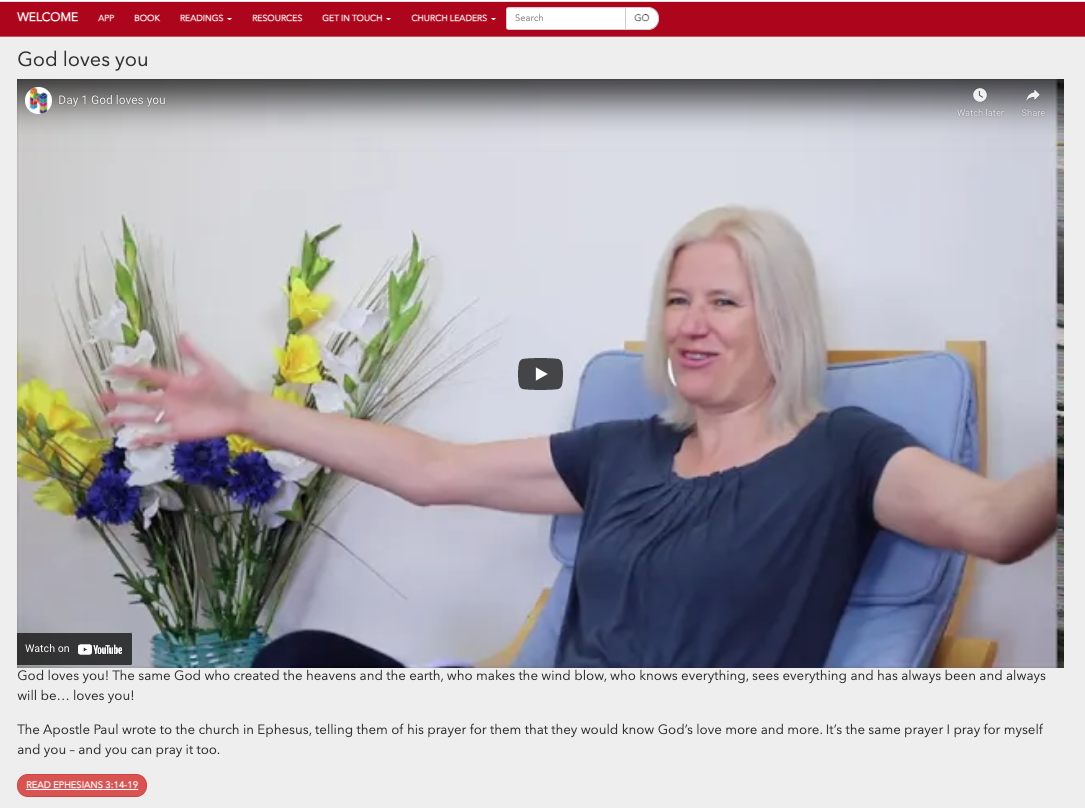
42 website and app
The 42 website and app is a project to deliver 42 days of content, to help new Christians grow in their faith.
The 42 days of content are delivered through a daily video and page of content on the website, in the app and a printed book. The app also has a messaging feature for a small group of people to ask and answer questions.
Boiler Service Reminders
My latest WordPress plugin is a boiler servicing reminder tool for plumbers.
Daniel wanted to remind his customers when they need their next annual boiler service, so they stay safe and legal (if a landlord). He wanted it to be automatic, so he could be freed up from remembering to chase customers and get on with servicing boilers and bigger projects for his loyal customer base. He has over 200 customers now, who keep coming back for their annual services.
The plugin is available now for your Plumbing website, or I can build you a website like Daniel’s at a very competitive price.
Interested? More details
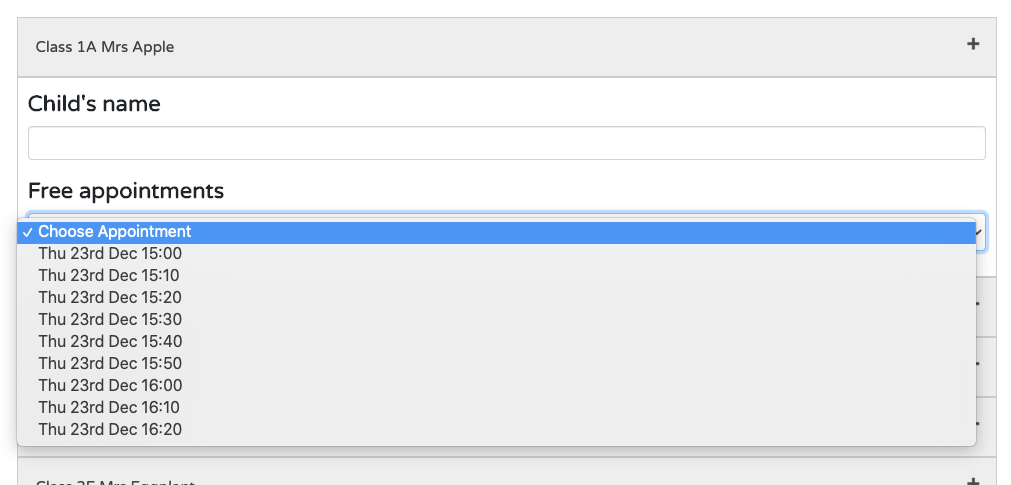
Parents Evening Booking System
I have created a simple secure parents evening booking system aimed at primary schools.
It’s a budget, but secure and simple to use solution for schools wanting to have online booking for parents evenings.
Admins can add classes and create parents evenings that span over several days with teachers breaks. Parents can book in and the booking form can be secured with your own “booking code” to protect you from spammers.
Interested?
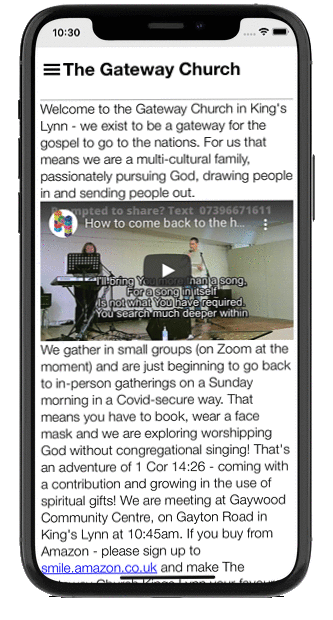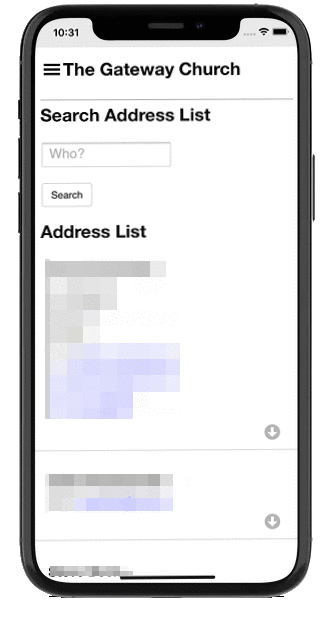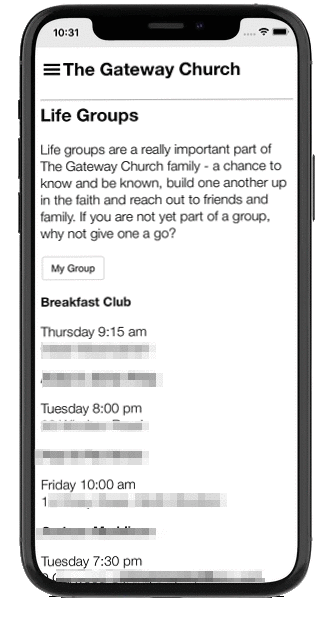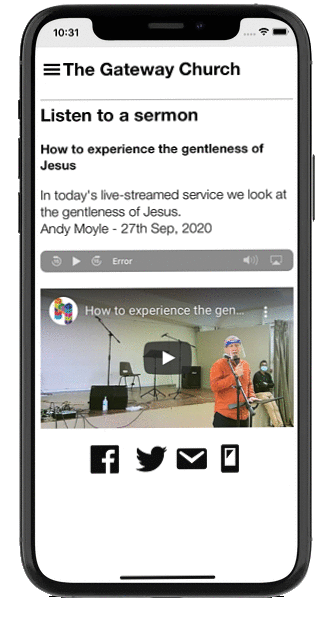
Church Management System
The Church Admin plugin and app is an ongoing WordPress plugin used by 1,000+ churches worldwide of varying sizes from 50-8,000.
It’s a powerful administrative tool to organise and communicate church life. Churches set up their address lists, rotas, calendar, ministries and much more, while staying GDPR compliant.
It also has a smartphone app that puts it all in the hands of the congregation.
Interested?
Our Church App
The Our Church app is available for iOS and Android devices.
The app put the power of the Church Admin plugin in the hands of the church congregation and includes push messaging, podcasting and member only features like address list and rotas.